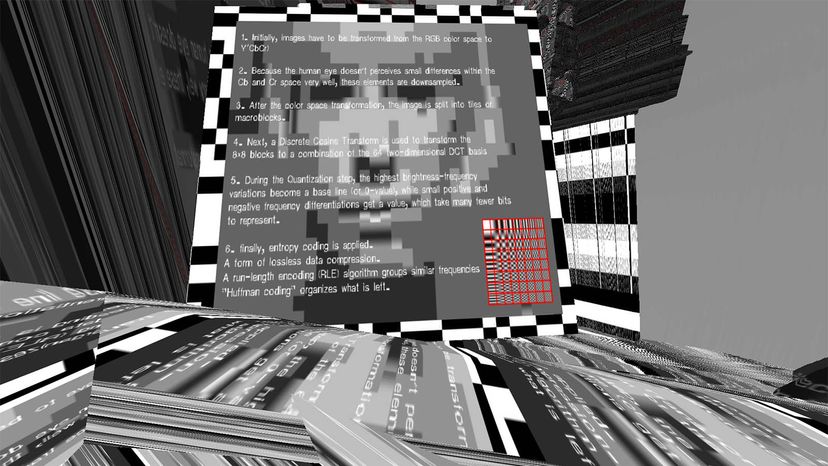
 Hidden in secret, a message can be transcoded and embedded on the surface of an image where it looks like an artifact, or part of the image.
Hidden in secret, a message can be transcoded and embedded on the surface of an image where it looks like an artifact, or part of the image.
And you thought your tattoos were provocative. In the year 499 B.C.E., Histiaeus — a Greek adviser to the Persian King Darius I — ordered an enslaved person to visit his son-in-law, Aristagoras. When the man arrived, he asked that his head be shaved.
There, tattooed on the enslaved person’s scalp, was a hidden message from Histiaeus. It told Aristagoras to instigate an uprising against none other than the Persian King himself, Darius I.
The adviser got his wish: Aristagoras stirred up the Ionian Revolt of 499 through 494 B.C.E. — Darius I ultimately prevailed, but the revolution catalyzed the Greco-Persian Wars (you know, the ones dramatized in the movie “300”).
By concealing those fighting words under a head of hair, Histiaeus became an early adopter of steganography. It’s a sneaky communication technique we’re still using today.
“Steganography” means “hidden writing.” Basically, this is the art of not only creating a secret message, but also hiding the message itself.
Histiaeus was plotting against his own ruler. Needless to say, the Greek had to tread carefully. He might have sent Aristagoras a letter like a normal person, sure. But such a note could be easily intercepted. Even if he’d used some kind of uncrackable code, the very fact that a man close to Darius I was dispatching coded letters at all would’ve raised eyebrows.
No, Histiaeus had to hide his message in a place where nobody would think to look for one, or recognize it for what it was. That’s steganography 101.
Advertisement
Obscurity and Security
Jessica Fridrich is a system scientist at Binghamton University in New York and an expert on steganography’s place in digital media.
“The power of steganography is that the very act of secret communication is not apparent,” she tells us via email.
Don’t confuse this with cryptography. A related but distinctive process, cryptography involves taking a piece of information and then trying to render it unintelligible to anyone besides the intended recipient(s).
Which is all well and good. Digital signatures rely on cryptography, as do mobile phones and automatic teller machines (ATMs).
Yet as computer scientist Simon R. Wiseman noted in a 2017 paper, this sort of communication “can be seen and it is obvious that some message is being passed, even though the message cannot be read.”
With steganography, it’s a whole new ballgame.
Advertisement
Staring Us in the Face
“Steganography can work in several different ways,” explains Fridrich. In one technique called steganography by cover modification, she says, “[an] existing image is modified to convey a desired message.”
With the right know-how, you could embed Shakespeare quotes inside an ordinary-looking digital cat photo. One method of doing so would involve modifying some of the pixels in a way that’s far too subtle for naked eyes to detect.
“Secretbook” capitalized on this concept. A Google Chrome browser extension unveiled in 2013, it allowed Facebook users to make incredibly slight alterations to JPEG images hosted on the social media platform. Through that process, participants could hide messages of 140 characters or fewer right inside the pictures — unbeknownst to (just about) anyone who didn’t have the password needed to reveal them.
Still images are great and all, but some folks would rather conceal their messages in computer audio files. People who use audio steganography have many tricks at their disposal, from hiding echoes to exploiting sound frequencies that lie above the normal human range of hearing.
Advertisement
Careful Crafting
In the wrong hands, steganography can be a destructive tool, as old Darius I found out.
Cyber attackers have been known to spread harmful malware by using stenographic techniques; think digital Trojan horses or remote access Trojan. Government agencies and private companies also need to be on-guard against hackers who infiltrate their websites and then leave dangerous data behind inside steganographic files.
“Steganalysis” is the practice of trying to detect and expose steganography. Sometimes, suspicious-looking files are inspected by algorithms designed especially for this purpose.
“Modern steganography uses powerful source coding to minimize the impact of the embedding changes,” says Fridrich. “Modern steganalysis is usually based on machine learning.”
(For those keeping score at home, machine learning is what happens when computers and algorithms learn from data and then make predictions accordingly. It’s an exciting field in the world of artificial intelligence.)
Steganography has trickled into our popular culture. In 2013, the Pew Research Center reported that “58% of [American] teen social media users say they share inside jokes or cloak their messages in some way.”
The practice might sound innocuous, but some say there’s a deeper meaning hiding under the surface. “As a way of creating a different sort of privacy,” notes the report, “many teen social media users will obscure some of their updates and posts, sharing … coded messages that only certain friends will understand.”
Communications scholars Danah Boyd and Alice E. Marwick call the phenomenon “social steganography.” Histiaeus would be proud.
Now That’s Interesting
If you look at the left field scoreboard at Boston’s Fenway Park, you may notice a series of painted dots and dashes. In Morse code, they spell out the initials “TAY” and “JRY” for former Red Sox owners Tom A. Yawkey and Jean R. Yawkey.
Advertisement